What is Civic?
Civic connects your AI assistant to all your tools - GitHub, Slack, Dropbox, databases, and dozens of other services. Your AI can finally do real work instead of just answering questions.How It Works
Easiest Way: Try It Directly in Civic Chat
Sign up at nexus.civic.com
Create your account and browse dozens of available MCP servers (GitHub, Slack, Dropbox, etc.)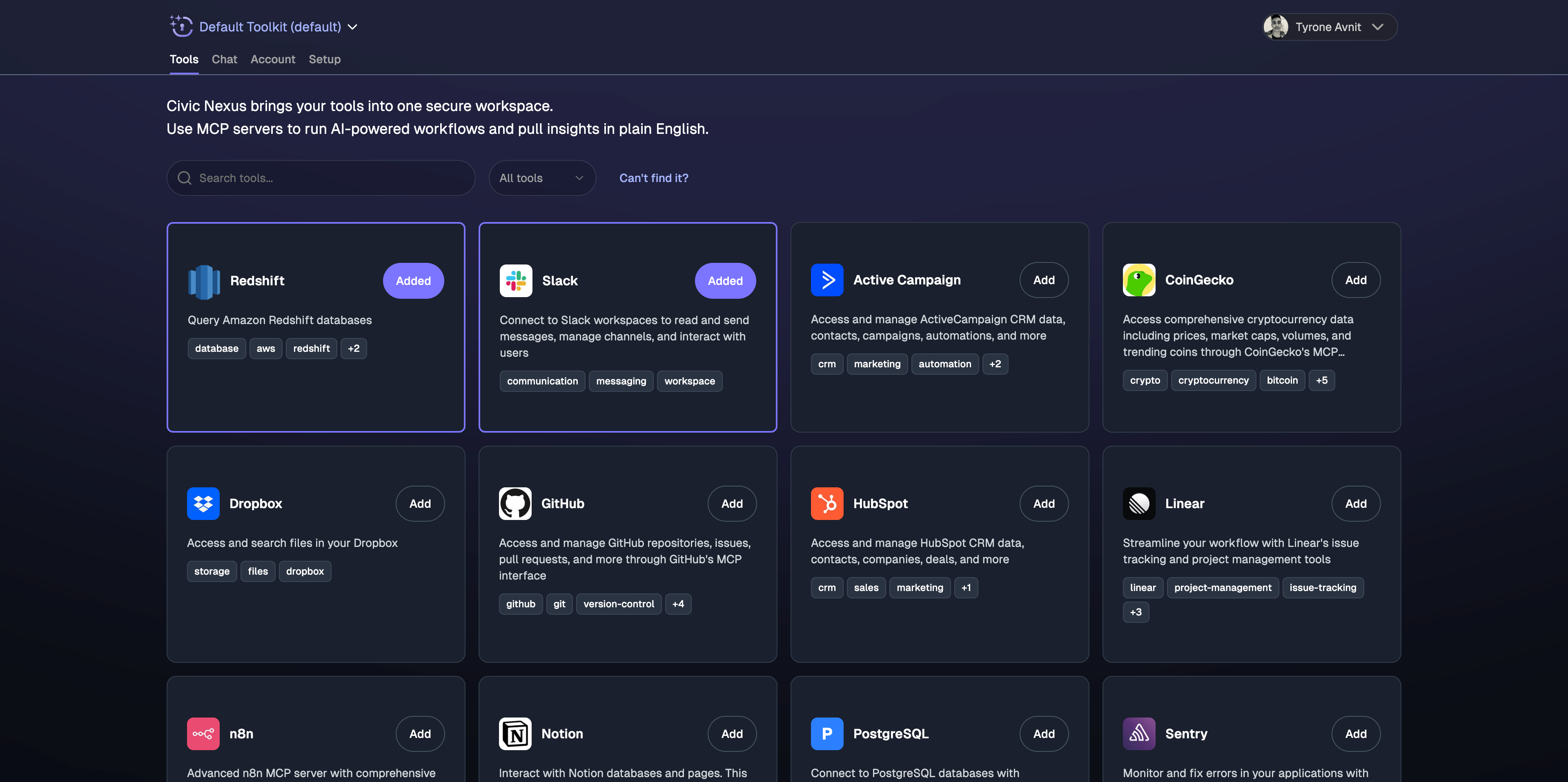

Click 'Chat' to test immediately
Use the built-in chat interface - no setup required, start testing tools right away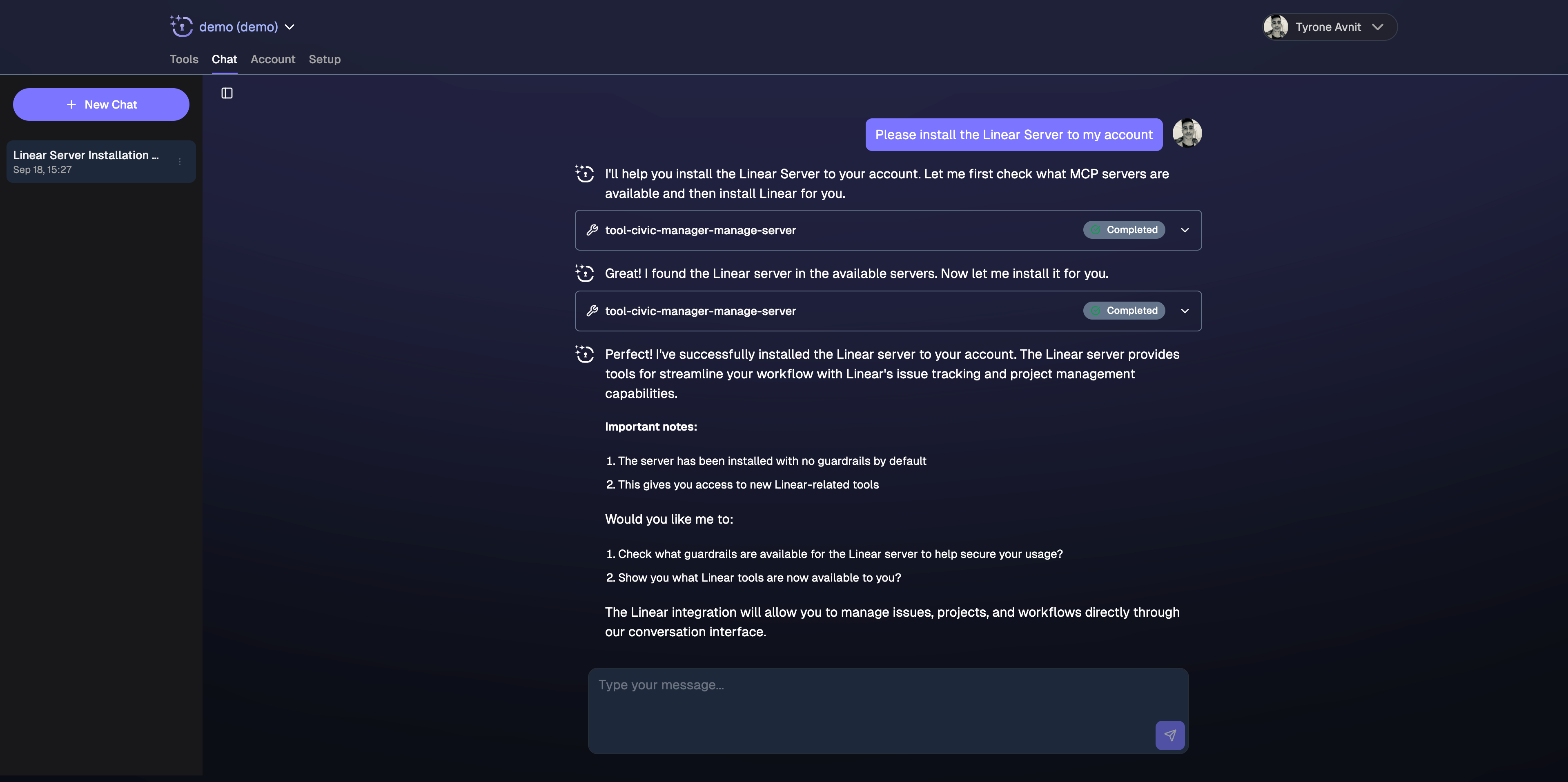

Ask for what you need
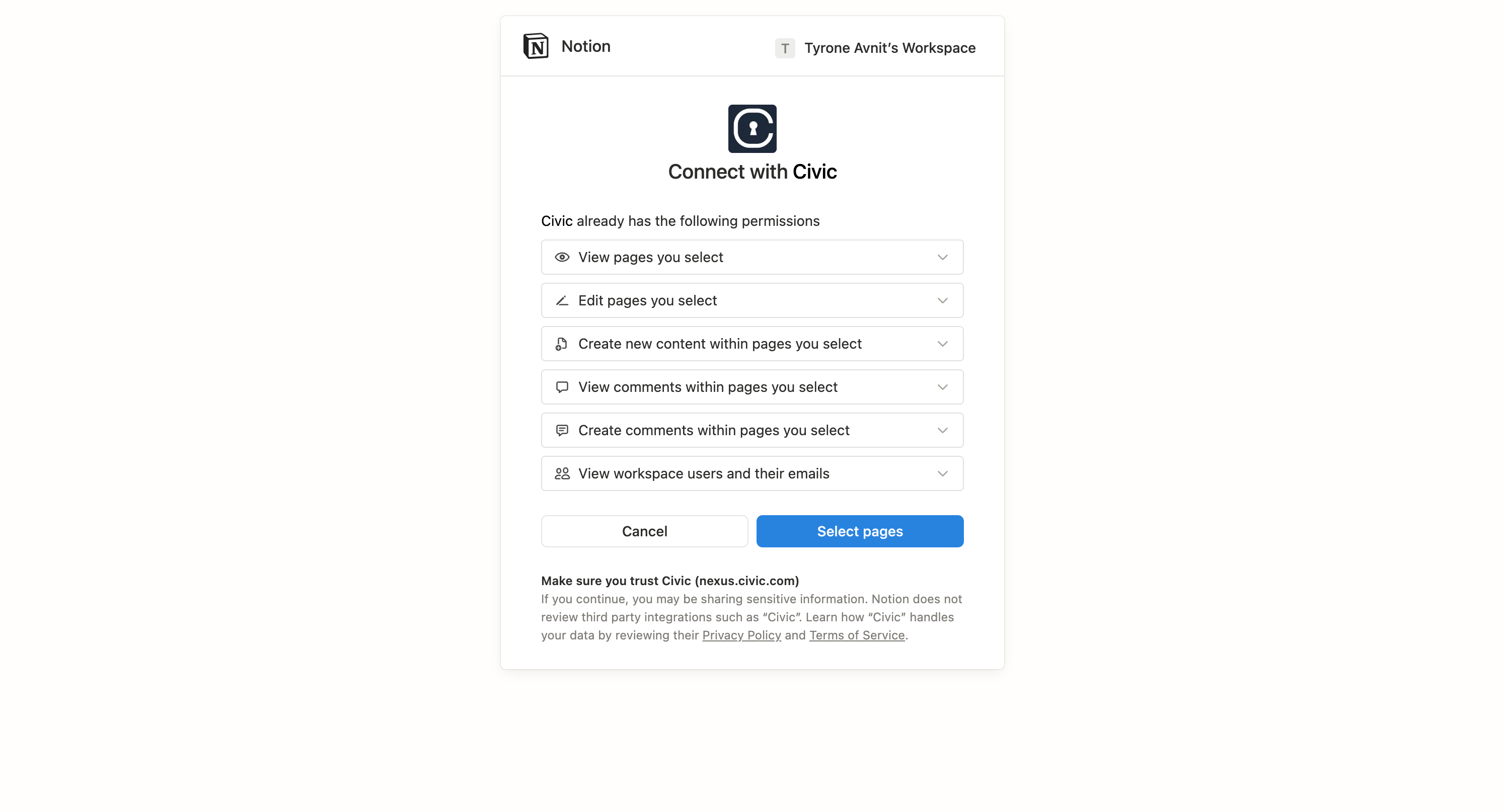
Request tools and authorizations directly in chat: “Connect me to GitHub”, “Check my Slack messages”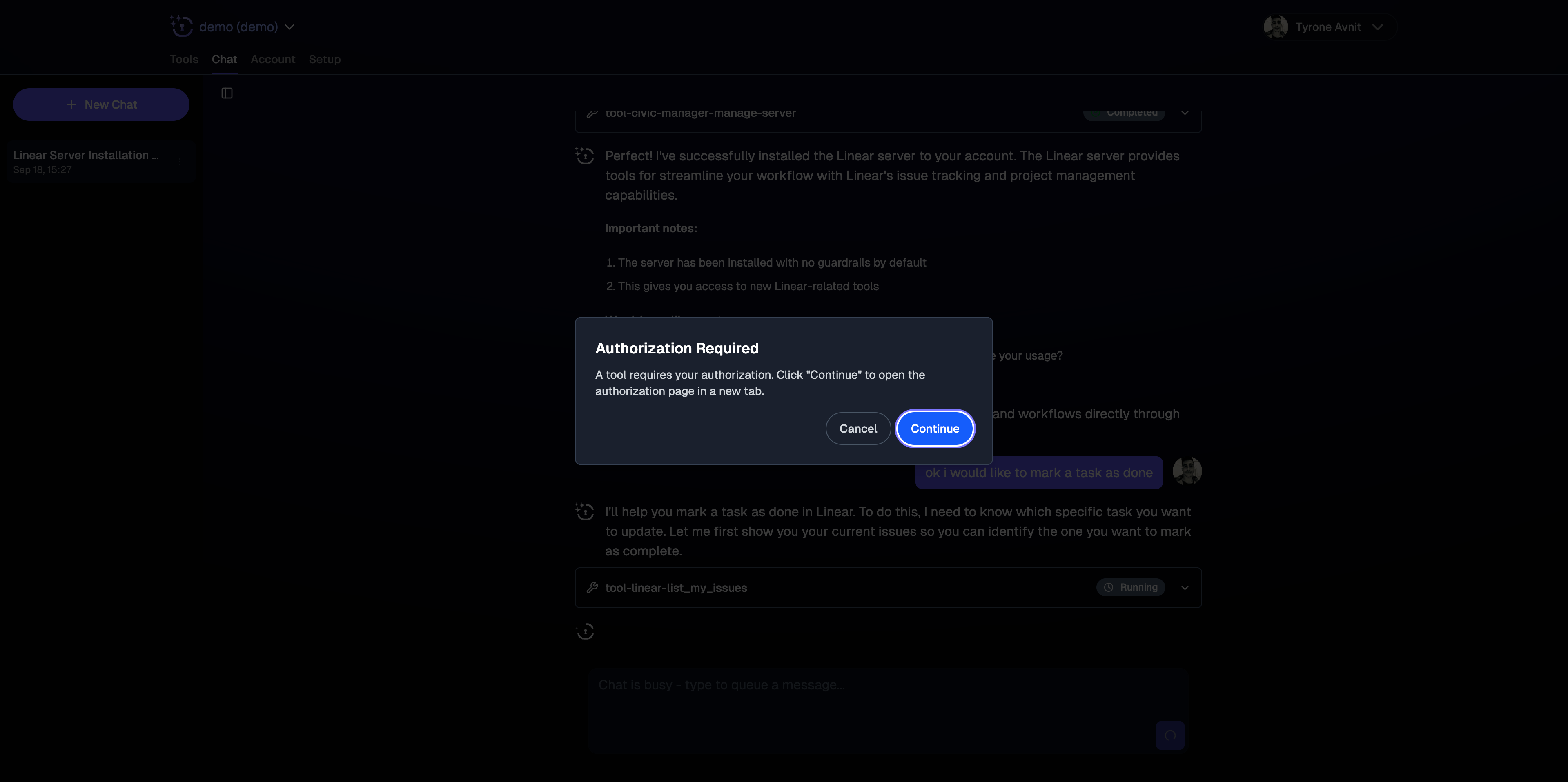

Optional: Connect External AI Clients
Once you’ve tested in Civic chat, you can connect external clients like Claude and development tools for convenience.No server management, no API keys to juggle, no complex configurations.
Claude Desktop
2 minutes - Most popular AI client
VS Code
2 minutes - Development IDE integration
Cursor
2 minutes - AI-powered code editor
Ready to Get Started?
Try Civic Chat Now
Fastest way - No setup required, start using tools immediately
Connect Your AI Client
For convenience - Use ChatGPT, Claude, or development tools
Start with Civic chat first - Test all tools directly in our interface, then optionally connect external AI clients for convenience.
What You Can Do
Once connected, your AI can work with all your tools:- For Developers
- For Teams
- For Marketing
- For RevOps
Organize Tools with Toolkits
Create focused groups of tools for specific workflows instead of overwhelming your AI with every available service.Why toolkits matter: When AI assistants have access to too many tools at once, they often choose the wrong ones or get confused. Toolkits solve this by creating focused, task-specific tool groups.
Marketing Analytics
Google Analytics + Notion + Slack for pulling data, documenting insights, and sharing reports
Developer Debugging
GitHub + PostgreSQL + Notion for investigating issues, querying databases, and documenting solutions
Learn About Toolkits
Create focused tool groups that help your AI work more effectively on specific tasks
Security
Your data security is our top priority. Civic is designed for more secure infrastructure with encrypted credential management and proactive server security reviews.
⚡ Full Control - Revoke app access instantly, changes apply immediately
🛡️ Encrypted Ease of Development - Streamlined development with stringent security standards
Security Details
Learn about our security architecture, compliance, and best practices
All Supported Clients
Primary AI Assistants
Claude Desktop
Available • Direct connector • 2 mins
Claude.ai
Available • Direct connector • 2 mins
Mistral LeChat
Available • Direct connector • 2 mins
Development Tools
Developer Setup Guide
Cursor, VS Code, JetBrains IDEs, and more - Advanced setup guides for development environments
Primary vs Development: Primary clients offer simple direct connector setup. Development tools require Hub Bridge configuration but offer the same functionality.
Get Started Right Now
Try Civic Chat Instantly
Zero setup required - Sign up and start using hundreds of tools in our built-in chat interface
Or Connect External Clients
Step-by-step guides for ChatGPT, Claude, VS Code, and more
Available Tools & Services
Connect to dozens of popular MCP servers with hundreds of tools:GitHub
Manage repos, create issues, review PRs
Slack
Send messages, search conversations
Dropbox
Access files, upload documents
Notion
Manage databases, create pages
Browse All Available Tools
Complete directory of MCP servers with setup guides